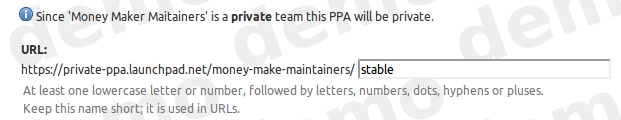
The Ubuntu Foundations team has sponsored work on various improvements to Launchpad’s archive handling lately, mainly to expose various new facilities on the API where we were previously using privileged scripts. This has involved cleaning up a substantial amount of old code along the way, and it has become possible to fix some other old bugs as spin-offs.
One of these old bugs is “Archive:+copy-packages nearly unusable due to timeouts”. The +copy-packages page allows anyone who can upload to a PPA to instead copy packages from another PPA. This saves effort, and in the “Copy existing binaries” mode it can save a substantial amount of build time as well. For example, the LibreOffice packaging team uses this to deliver packages to different sets of users after they have passed various levels of testing.
Unfortunately, the very cases where this is most useful, namely large and complex packages, are also the cases where it is most likely to break. Copying large numbers of binary packages involves large numbers of database queries and can quite easily overrun the timeout for a single request to the Launchpad web application. Doing this for several series at once, a common case which seems reasonable, is proportionally less likely to work. Various attempts have been made to optimise the database interactions here, but ultimately doing lots of complex synchronous work in time for a single web request is doomed to failure.
The solution to all this is to copy packages asynchronously. For some time Launchpad has had the ability to schedule “package copy jobs” which run very shortly after the request (typically within a minute) but not immediately. For example, the Ubuntu team uses these when copying new versions of packages from Debian unstable in cases where there are no Ubuntu-specific modifications, and when releasing proposed updates to stable releases for general use after verification. A similar facility has been present in the code for the +copy-packages page for some time, but not exposed due to various bugs. We believe that these bugs have been fixed now, and so we would like to start copying packages asynchronously when requested via the web UI.
We have exposed this to beta testers first. The effect is that, if you are a beta tester when you ask for packages to be copied, you will be told something like “Requested sync of 2 packages. Please allow some time for these to be processed.” The processing should normally happen within a minute or two, and you will be able to see it in progress on the +packages page for the target archive. If it succeeds, the in-progress notification will be removed and you will be able to see the changes in the target archive. Otherwise, you will see a failure notification along these lines:
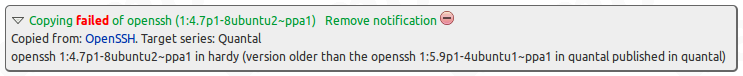
If beta-testing goes well, then we will enable this for all users, and remove the old synchronous copying code shortly afterwards; so please do report any problems you see.
If you are relying on package copies in the web UI happening immediately rather than within a few minutes, firstly, please contact us (e.g. #launchpad-dev on freenode IRC, or launchpad-users@lists.launchpad.net) as we would like to understand your requirements in more detail; secondly, you may be able to use the Archive.syncSource API method instead, which also has timeout constraints but is at least guaranteed to remain synchronous. However, we hope that most people will not have such a requirement.